How To Install Ntp Server On Windows 2012 Service
Windows-time-server-Default-time-sync-behavior-in-Active-Directory.png' alt='How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />Server hardening By submitting your personal information, you agree that Tech. Target and its partners may contact you regarding relevant content, products and special offers. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. Server hardening. Server hardening consists of creating a baseline for the security on your servers in your organization. The default configurations of a Windows Server 2. Rather, a default installed computer is designed for communication and functionality. To protect your servers, you must establish solid and sophisticated security policies for all types of servers in your organization. In this section, we will discuss the basic security baseline for a member server that is running in a Windows Server 2. Active Directory domain. We will also discuss the best practice security configurations in the security templates, starting with the generic best practices that apply to most member servers in the organization. We will then move on to the specific types of member servers, as well as domain controllers. We will discuss which services, ports, applications, and so forth need to be hardened for different server roles, and compare this to the baseline security for simple member servers. Member servers. You must establish a baseline of security for all members servers before creating additional security templates and policies to tailor security for specific types of servers. One of the most important aspects of applying hardening settings to member servers is developing the OU hierarchy that will support the security template and policies that you develop. You must also understand the various levels of security that are routinely used to develop and deploy security to all servers. Gee, setting up an SNTPNTP server in Windows is not intuitive. The good news is When configured correctly, you can use the Windows Time W32Time service as an SNTP. How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />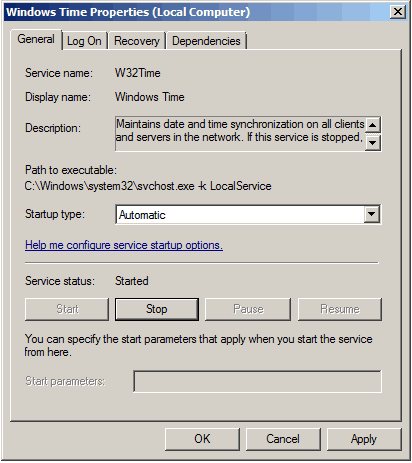 OU design considerations. The only way to efficiently and successfully deploy security to the different server roles in your enterprise is to design Active Directory to support those roles. The design should not only provide an efficient method to deploy security, but it should also organize the computer accounts into OUs for easier management and troubleshooting. Although Active Directory design is extremely flexible, you must consider a number of factors when organizing servers into OUs based on server role. ZZh_dUALIY/UHewceAzIkI/AAAAAAAAAdE/5a9dONj0E20/s1600/ntp5.JPG' alt='How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />This article shows how to configure Windows Time Service on Windows Server 2016 so that it acts as an NTP server for domain client computers. Configure Windows Time. Event ID 1004 IPMI Driver Functionality Source IPMIDRV Type Error Description The IPMI device driver attempted to communicate with the IPMI BMC. BlackBerry smartphones can be integrated into an organizations email system through a software package called BlackBerry Enterprise Server BES through version 5. Overview. The Windows Time service is a component which uses a plugin model for client and server time synchronization providers. There are two builtin client. The first factor is Group Policy application. For example, if you have two server roles that each need different security policy settings, you should separate the computer accounts into different OUs. The second factor is administration of the computer accounts within Active Directory. Even though you have only two different server roles, you might have two different administrators controlling the same type of server role. This might force you to have OUs not only for server roles, but also for server roles based on the administrator in charge. Figures 5 7 illustrates an OU structure that does not consider location or administrative needs but does consider server roles. Figure 5 8 illustrates an OU structure that has a different set of administrators for the Main Office and Branch Office, where each office also has the same types of server roles. How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />Figure 5 7 An OU structure based on server roles only. Figure 5 8 An OU structure that considers location and administrative needs as well as server roles. TIP OUs are also commonly organized by physical location for example, the Main Office and Branch Office model. For more information on organizing OUs based on GPO deployment, see Chapter 4. Member server security environment levels. Member server security environments are based on the operating systems of the clients and servers in your enterprise. Legacy clients and servers cant take advantage of the robust features and functions that Active Directory provides, such as Group Policy, Kerberos, and other security features. As the operating systems of domain members rise to levels that support all Active Directory functions and features, it becomes possible to raise the overall security for the enterprise and thus create a solid security environment. There are three different security environment levels typically found in an enterprise environment Legacy Client When you have a mixed operating system environment of new and older versions, you must provide adequate security that will not constrain the operation of legacy clients. This is the lowest security level, but it needs to be that way for communication to occur and legacy applications to work properly. This business environment might include legacy clients such as Windows 9. Windows 9. 8, or Windows NT 4. Workstation. You should limit this environment to having only Windows 2. Server and Windows Server 2. You should not support Windows NT 4. Server domain controllers, although you can have Windows NT Server computers configured as member servers. Enterprise Client This security level removes the legacy operating systems and uses only those that support the features and functions that Active Directory offers. This includes clients running Windows 2. Professional and Windows XP Professional. These clients all support Group Policy, Kerberos authentication, and new security features that the legacy clients dont support. The domain controllers must be Windows 2. Server or later. There will not be any Windows NT Server computers, even as member servers. High Security This security level is basically the same as for Enterprise Client it changes only the level of security that is implemented. This level enhances security standards so that all computers conform to stringent security policies for both clients and servers. This environment might be constrictive enough that loss of functionality and manageability occurs. However, this must be acceptable because the higher security levels are a good tradeoff for the functionality and manageability that you are losing. Lisa Ann Sucking'>Lisa Ann Sucking. Windows Server 2. Security GuideThe three enterprise environments described earlier and the procedures outlined in this chapter for hardening different server roles in each environment are discussed more fully in the Windows Server 2. Security Guide. The Security Guide also includes a set of additional security templates that can be imported into GPOs to harden different server roles in legacy client, enterprise client, and high security environments. Shoot A Thon Fundraiser Template Microsoft. It also includes additional procedures for hardening security settings that cannot be configured using Group Policy. Using these additional security templates can simplify the hardening of different server roles on your network, and you can further customize these security templates to meet the specific needs of your Active Directory environment. Security settings for member servers. This section will cover some common security settings that apply to standard member servers in the domain. These settings are best created in a GPO that is then linked to the top level server OU. In Figure 5 7 or 5 8, this would be the Member Servers OU. Table 5 7 provides a full list of security settings for a member server. NOTE Account Policies, which include Password Policy, Account Lockout Policy, and Kerberos Policy, are not specified in the member servers security baseline outlined here. This is because Account Policies must be defined at the domain level in Active Directory, while the member servers security baseline is defined in GPOs linked to OUs where member servers are found. How can I query an NTP server under Windows I am not interested in synchronizing my local clock with the remote server. I only want to query it and print the result. I would have assumed that there is a port of ntpq for Windows, but was unable to find any. All other NTP clients I could find, they always want to install themselves as a service or make it otherwise clear that they want to synchronize my local time.
OU design considerations. The only way to efficiently and successfully deploy security to the different server roles in your enterprise is to design Active Directory to support those roles. The design should not only provide an efficient method to deploy security, but it should also organize the computer accounts into OUs for easier management and troubleshooting. Although Active Directory design is extremely flexible, you must consider a number of factors when organizing servers into OUs based on server role. ZZh_dUALIY/UHewceAzIkI/AAAAAAAAAdE/5a9dONj0E20/s1600/ntp5.JPG' alt='How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />This article shows how to configure Windows Time Service on Windows Server 2016 so that it acts as an NTP server for domain client computers. Configure Windows Time. Event ID 1004 IPMI Driver Functionality Source IPMIDRV Type Error Description The IPMI device driver attempted to communicate with the IPMI BMC. BlackBerry smartphones can be integrated into an organizations email system through a software package called BlackBerry Enterprise Server BES through version 5. Overview. The Windows Time service is a component which uses a plugin model for client and server time synchronization providers. There are two builtin client. The first factor is Group Policy application. For example, if you have two server roles that each need different security policy settings, you should separate the computer accounts into different OUs. The second factor is administration of the computer accounts within Active Directory. Even though you have only two different server roles, you might have two different administrators controlling the same type of server role. This might force you to have OUs not only for server roles, but also for server roles based on the administrator in charge. Figures 5 7 illustrates an OU structure that does not consider location or administrative needs but does consider server roles. Figure 5 8 illustrates an OU structure that has a different set of administrators for the Main Office and Branch Office, where each office also has the same types of server roles. How To Install Ntp Server On Windows 2012 Service' title='How To Install Ntp Server On Windows 2012 Service' />Figure 5 7 An OU structure based on server roles only. Figure 5 8 An OU structure that considers location and administrative needs as well as server roles. TIP OUs are also commonly organized by physical location for example, the Main Office and Branch Office model. For more information on organizing OUs based on GPO deployment, see Chapter 4. Member server security environment levels. Member server security environments are based on the operating systems of the clients and servers in your enterprise. Legacy clients and servers cant take advantage of the robust features and functions that Active Directory provides, such as Group Policy, Kerberos, and other security features. As the operating systems of domain members rise to levels that support all Active Directory functions and features, it becomes possible to raise the overall security for the enterprise and thus create a solid security environment. There are three different security environment levels typically found in an enterprise environment Legacy Client When you have a mixed operating system environment of new and older versions, you must provide adequate security that will not constrain the operation of legacy clients. This is the lowest security level, but it needs to be that way for communication to occur and legacy applications to work properly. This business environment might include legacy clients such as Windows 9. Windows 9. 8, or Windows NT 4. Workstation. You should limit this environment to having only Windows 2. Server and Windows Server 2. You should not support Windows NT 4. Server domain controllers, although you can have Windows NT Server computers configured as member servers. Enterprise Client This security level removes the legacy operating systems and uses only those that support the features and functions that Active Directory offers. This includes clients running Windows 2. Professional and Windows XP Professional. These clients all support Group Policy, Kerberos authentication, and new security features that the legacy clients dont support. The domain controllers must be Windows 2. Server or later. There will not be any Windows NT Server computers, even as member servers. High Security This security level is basically the same as for Enterprise Client it changes only the level of security that is implemented. This level enhances security standards so that all computers conform to stringent security policies for both clients and servers. This environment might be constrictive enough that loss of functionality and manageability occurs. However, this must be acceptable because the higher security levels are a good tradeoff for the functionality and manageability that you are losing. Lisa Ann Sucking'>Lisa Ann Sucking. Windows Server 2. Security GuideThe three enterprise environments described earlier and the procedures outlined in this chapter for hardening different server roles in each environment are discussed more fully in the Windows Server 2. Security Guide. The Security Guide also includes a set of additional security templates that can be imported into GPOs to harden different server roles in legacy client, enterprise client, and high security environments. Shoot A Thon Fundraiser Template Microsoft. It also includes additional procedures for hardening security settings that cannot be configured using Group Policy. Using these additional security templates can simplify the hardening of different server roles on your network, and you can further customize these security templates to meet the specific needs of your Active Directory environment. Security settings for member servers. This section will cover some common security settings that apply to standard member servers in the domain. These settings are best created in a GPO that is then linked to the top level server OU. In Figure 5 7 or 5 8, this would be the Member Servers OU. Table 5 7 provides a full list of security settings for a member server. NOTE Account Policies, which include Password Policy, Account Lockout Policy, and Kerberos Policy, are not specified in the member servers security baseline outlined here. This is because Account Policies must be defined at the domain level in Active Directory, while the member servers security baseline is defined in GPOs linked to OUs where member servers are found. How can I query an NTP server under Windows I am not interested in synchronizing my local clock with the remote server. I only want to query it and print the result. I would have assumed that there is a port of ntpq for Windows, but was unable to find any. All other NTP clients I could find, they always want to install themselves as a service or make it otherwise clear that they want to synchronize my local time.